Case Examples Organized by Covered Entity. Here are some other examples of HIPAA violations.
 Hipaa Violations In The News How To Avoid Them
Hipaa Violations In The News How To Avoid Them
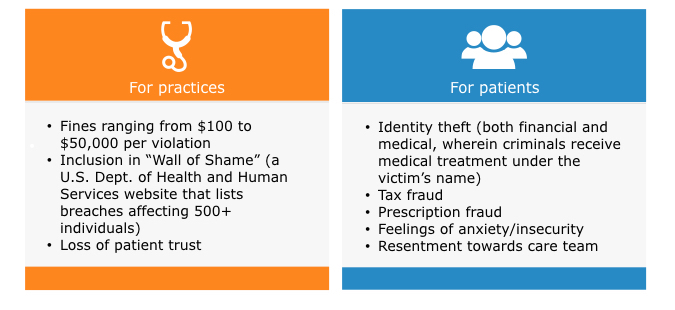
The most common HIPAA violations that have resulted in financial penalties are the failure to perform an organization-wide risk analysis to identify risks to the confidentiality integrity and availability of protected health information PHI.

Hipaa breach examples. Employee discipline for a HIPAA violation depends on the type of breach that occurred. A breach refers to the unauthorized acquisition access use or disclosure of protected health information. The HIPAA Breach Notification Rule stipulates that all PHI breaches must be reported except in the following situations.
And the failure to safeguard PHI. If you have any other questions that we havent included please feel free to leave them in the comments section below and well get back to you. Huping Zhou snooped into the medical records of four high-profile celebrities.
Weve seen examples of intentional violations that date all the way back to 2003 when Dr. There are three levels of a breach that weve defined each of which has its own employee penalty. Also located in Texas a cancer center paid over 43 million in civil monetary penalties after three data breaches that violated HIPAA.
HIPAA Violations FAQ. Not to mention a more recent breach we saw happen where a healthcare worker purposefully leak the medical information of someone who was dating her ex-boyfriend on social media. Lets look at some of the recent HIPAA breach examples.
Describe the types of PHI involved in the breach. 1 unintentional acquisition access or use of PHI in good faith 2 inadvertent disclosure to an authorized person at the same organization 3 the receiver is unable to retain the PHI. Type s of PHI compromised.
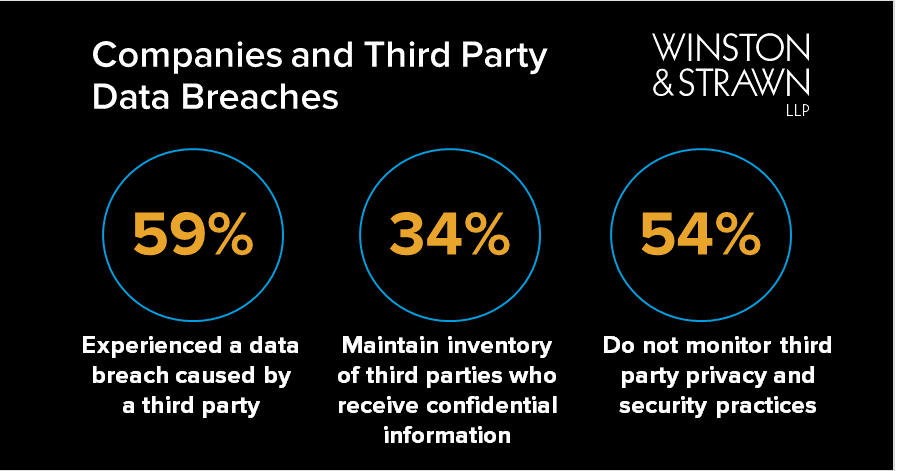
North Memorial Health Care of Minnesota had to pay 155 million in a settlement for failing to enter into a Business Associate Agreement with a major contractor. According to the HIPAA Breach Notification Rule 45 CFR 164400-414 breaches involving electronic or physical copies of protected health information must be reported by covered entities and their business associates. Breach definitions and their recommended disciplinary action should exist within your policy manual.
If the nurse were to then look at their chart to see the purpose of their visit this is considered a breach. Here are the top ten most common HIPAA violations. This may include the patients full name social security number date of birth home address account number diagnosis disability code or other types of information.
One of the incidents involved an unencrypted laptop that was stolen from an employee vehicle and another incident involved the theft of four computers. Impermissible disclosures of PHI. Two examples of well-meaning staff breaching HIPAA might include if a nurse notices their neighbor in the hospital.
Health Plans HMOs. Steps the individual should take. This is the largest HIPAA settlement as of September 2016 and was the result of three separate data breaches that affected a total of 4 million individuals.
There are 3 exceptions. What are Common Examples of HIPAA Infractions. The examples below show 20 cases where healthcare employees violated the HIPAA law.
The University of California Los Angeles Health System was fined 865000for failing to restrict access to medical records. Not every impermissible disclosure of PHI is a HIPAA breach. The Office of Civil Rights investigation revealed that three devices were stolen resulting in a breach of PHI for over 34000 patients.
Compromised email account Oregon-based Santa Rosa Rohnert Park Oral Surgery recently detected that an outsider accessed one of its employees email accounts without authorization. The failure to enter into a HIPAA-compliant business associate agreement. Violations can involve texting social media mishandling of records illegal access of patient files or breaches that arise from social situations.
An unintentional acquisition access or use of PHI by a workforce member or person acting under the authority of a covered entity or business associate if such acquisition access or use was made in good faith and within the scope of authority. Frequently HIPAA violations stem not from malicious intent but from a poor understanding of the law itself. To end this post we have put together a few additional Frequently Asked Questions.